https://portswigger.net/web-security/learning-paths/server-side-vulnerabilities-apprentice
This learning path introduces you to a range of common server-side vulnerabilities. This is perfect if you’re new to web security and want to get an overview of the kinds of vulnerabilities that exist, as well as how an attacker might identify and exploit them in real-world systems.
Attacks:
- Path traversal
- Access control
- Authentication
- Server-side request forgery (SSRF)
- File upload vulnerabilities (Part 2)
- OS command injection (Part 2)
- SQL injection (Part 2)
Go to part 2.
Path traversal
Path traversal is also known as directory traversal. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. This might include:
Application code and data.
Credentials for back-end systems.
Sensitive operating system files.In some cases, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behavior, and ultimately take full control of the server.
For instance, we have:
<img src="/loadImage?filename=218.png">The image files are stored on disk in the location /var/www/images/.
This application implements no defenses against path traversal attacks. As a result, an attacker can request the following URL to retrieve the /etc/passwd file from the server’s filesystem: https://insecure-website.com/loadImage?filename=../../../etc/passwd
The sequence ../ is valid within a file path, and means to step up one level in the directory structure. The three consecutive ../ sequences step up from /var/www/images/ to the filesystem root, and so the file that is actually read is: /etc/passwd
LAB:
This lab contains a path traversal vulnerability in the display of product images. To solve the lab, retrieve the contents of the /etc/passwd file.
Solution:
To solve this, I started by right-clicking an image to grab its source URL. That gave me something like:
0aaf00eb033990da81ca5247006800a9.web-security-academy.net/image?filename=8.jpgThen, I just kept adding ../ to the filename parameter a few times until I found the directory I was looking for.
The solution ended up being:
https://0aaf00eb033990da81ca5247006800a9.web-security-academy.net/image?filename=../../../etc/passwdAccess control
Access control is the application of constraints on who or what is authorized to perform actions or access resources. In the context of web applications, access control is dependent on authentication and session management:
Authentication confirms that the user is who they say they are. Session management identifies which subsequent HTTP requests are being made by that same user. Access control determines whether the user is allowed to carry out the action that they are attempting to perform.
Vertical privilege escalation If a user can gain access to functionality that they are not permitted to access then this is vertical privilege escalation. For example, if a non-administrative user can gain access to an admin page where they can delete user accounts, then this is vertical privilege escalation.
At its most basic, vertical privilege escalation arises where an application does not enforce any protection for sensitive functionality. For example, administrative functions might be linked from an administrator’s welcome page but not from a user’s welcome page. However, a user might be able to access the administrative functions by browsing to the relevant admin URL.
For example, a website might host sensitive functionality at the following URL: https://insecure-website.com/admin This might be accessible by any user, not only administrative users who have a link to the functionality in their user interface. In some cases, the administrative URL might be disclosed in other locations, such as the robots.txt file: https://insecure-website.com/robots.txt
Even if the URL isn’t disclosed anywhere, an attacker may be able to use a wordlist to brute-force the location of the sensitive functionality.
LAB: Unprotected admin functionality
This lab has an unprotected admin panel. Solve the lab by deleting the user carlos.
Solution:
I found the /administrator-panel by checking /robots.txt. Turns out, you can delete users from there.
Unprotected functionality - Continued
In some cases, sensitive functionality is concealed by giving it a less predictable URL. This is an example of so-called “security by obscurity”. However, hiding sensitive functionality does not provide effective access control because users might discover the obfuscated URL in a number of ways.
Imagine an application that hosts administrative functions at the following URL: https://insecure-website.com/administrator-panel-yb556 This might not be directly guessable by an attacker. However, the application might still leak the URL to users. The URL might be disclosed in JavaScript that constructs the user interface based on the user’s role:
<script>
var isAdmin = false;
if (isAdmin) {
...
var adminPanelTag = document.createElement('a');
adminPanelTag.setAttribute('href', 'https://insecure-website.com/administrator-panel-yb556');
adminPanelTag.innerText = 'Admin panel';
...
}
</script>Lab: Unprotected admin functionality with unpredictable URL
This lab has an unprotected admin panel. It’s located at an unpredictable location, but the location is disclosed somewhere in the application.
Solve the lab by accessing the admin panel, and using it to delete the user carlos.
Solution:
I found the admin panel directory by viewing the page’s source code. Inside, there was a JavaScript snippet: JavaScript
if (isAdmin) {
var topLinksTag = document.getElementsByClassName("top-links")[0];
var adminPanelTag = document.createElement('a');
adminPanelTag.setAttribute('href', '/admin-6qx1ng');
}I used /admin-6qx1ng to get into the admin panel.
Parameter-based access control methods Some applications determine the user’s access rights or role at login, and then store this information in a user-controllable location. This could be:
- A hidden field.
- A cookie.
- A preset query string parameter.
The application makes access control decisions based on the submitted value. For example: https://insecure-website.com/login/home.jsp?admin=true https://insecure-website.com/login/home.jsp?role=1
This approach is insecure because a user can modify the value and access functionality they’re not authorized to, such as administrative functions.
Lab:
This lab has an admin panel at /admin, which identifies administrators using a forgeable cookie. Solve the lab by accessing the admin panel and using it to delete the user carlos. You can log in to your own account using the following credentials: wiener
Solution;
I used the browser’s developer tools to grab the cookie. Then, in Burp Suite’s Repeater, I sent a new request and changed the admin cookie’s value from false to true. After rendering the response and reading the raw output, I discovered that deleting an account was done via:
GET /admin/delete?username=carlos
So, I sent that request to delete the user.
Horizontal privilege escalation
Horizontal privilege escalation occurs if a user is able to gain access to resources belonging to another user, instead of their own resources of that type. For example, if an employee can access the records of other employees as well as their own, then this is horizontal privilege escalation.
Horizontal privilege escalation attacks may use similar types of exploit methods to vertical privilege escalation. For example, a user might access their own account page using the following URL: https://insecure-website.com/myaccount?id=123
LAB:
This lab has a horizontal privilege escalation vulnerability on the user account page, but identifies users with GUIDs.
To solve the lab, find the GUID for carlos, then submit his API key as the solution.
You can log in to your own account using the following credentials: wiener
profile page is https://0abb008404111cbd80214eba008300f1.web-security-academy.net/my-account?id=lalalal
Solution:
In the blog we can see who is the author of each post. Their profile webaddress gives their id. So we can replace our ID for their’s.
Horizontal to vertical privilege escalation
Often, a horizontal privilege escalation attack can be turned into a vertical privilege escalation, by compromising a more privileged user. For example, a horizontal escalation might allow an attacker to reset or capture the password belonging to another user. If the attacker targets an administrative user and compromises their account, then they can gain administrative access and so perform vertical privilege escalation.
An attacker might be able to gain access to another user’s account page using the parameter tampering technique already described for horizontal privilege escalation: https://insecure-website.com/myaccount?id=456
If the target user is an application administrator, then the attacker will gain access to an administrative account page. This page might disclose the administrator’s password or provide a means of changing it, or might provide direct access to privileged functionality.
LAB:
This lab has user account page that contains the current user’s existing password, prefilled in a masked input. To solve the lab, retrieve the administrator’s password, then use it to delete the user carlos. You can log in to your own account using the following credentials: wiener
Solution:
In https://0afa00d704bc20c0cef51719002200c7.web-security-academy.net/my-account?id=wiener we change our username for “administrator”. There we can read the password.
Authentication vulnerabilities
Conceptually, authentication vulnerabilities are easy to understand. However, they are usually critical because of the clear relationship between authentication and security.
Authentication vulnerabilities can allow attackers to gain access to sensitive data and functionality. They also expose additional attack surface for further exploits. For this reason, it’s important to learn how to identify and exploit authentication vulnerabilities, and how to bypass common protection measures.
In this section, we explain:
- The most common authentication mechanisms used by websites.
- Potential vulnerabilities in these mechanisms.
- Inherent vulnerabilities in different authentication mechanisms.
- Typical vulnerabilities that are introduced by their improper implementation.
- How you can make your own authentication mechanisms as robust as possible.
What is the difference between authentication and authorization?
Authentication is the process of verifying that a user is who they claim to be. Authorization involves verifying whether a user is allowed to do something.
For example, authentication determines whether someone attempting to access a website with the username Carlos123 really is the same person who created the account.
Once Carlos123 is authenticated, their permissions determine what they are authorized to do. For example, they may be authorized to access personal information about other users, or perform actions such as deleting another user’s account.
Brute-force attacks
A brute-force attack is when an attacker uses a system of trial and error to guess valid user credentials. These attacks are typically automated using wordlists of usernames and passwords. Automating this process, especially using dedicated tools, potentially enables an attacker to make vast numbers of login attempts at high speed.
Brute-forcing is not always just a case of making completely random guesses at usernames and passwords. By also using basic logic or publicly available knowledge, attackers can fine-tune brute-force attacks to make much more educated guesses.
Brute-forcing usernames
Usernames are especially easy to guess if they conform to a recognizable pattern, such as an email address. For example, it is very common to see business logins in the format firstname.lastname@somecompany.com. However, even if there is no obvious pattern, sometimes even high-privileged accounts are created using predictable usernames, such as admin or administrator.
During auditing, check whether the website discloses potential usernames publicly. For example, are you able to access user profiles without logging in? Even if the actual content of the profiles is hidden, the name used in the profile is sometimes the same as the login username. You should also check HTTP responses to see if any email addresses are disclosed. Occasionally, responses contain email addresses of high-privileged users, such as administrators or IT support.
Brute-forcing passwords
Passwords can similarly be brute-forced, with the difficulty varying based on the strength of the password. Many websites adopt some form of password policy, which forces users to create high-entropy passwords that are, theoretically at least, harder to crack using brute-force alone. This typically involves enforcing passwords with:
- A minimum number of characters
- A mixture of lower and uppercase letters
- At least one special character
Brute-forcing passwords - Continued
However, while high-entropy passwords are difficult for computers alone to crack, we can use a basic knowledge of human behavior to exploit the vulnerabilities that users unwittingly introduce to this system. Rather than creating a strong password with a random combination of characters, users often take a password that they can remember and try to crowbar it into fitting the password policy. For example, if mypassword is not allowed, users may try something like Mypassword1! or Myp4$$w0rd instead.
In cases where the policy requires users to change their passwords on a regular basis, it is also common for users to just make minor, predictable changes to their preferred password. For example, Mypassword1! becomes Mypassword1? or Mypassword2!.
This knowledge of likely credentials and predictable patterns means that brute-force attacks can often be much more sophisticated, and therefore effective, than simply iterating through every possible combination of characters.
Username enumeration
Username enumeration is when an attacker is able to observe changes in the website’s behavior in order to identify whether a given username is valid.
Username enumeration typically occurs either on the login page, for example, when you enter a valid username but an incorrect password, or on registration forms when you enter a username that is already taken. This greatly reduces the time and effort required to brute-force a login because the attacker is able to quickly generate a shortlist of valid usernames.
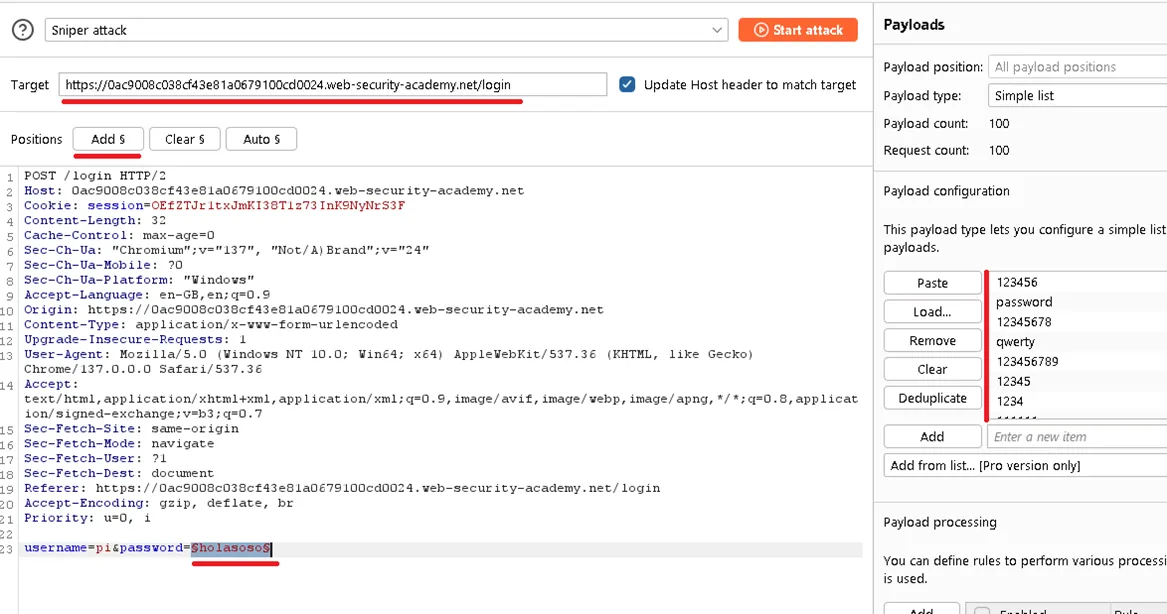
Lab: Username enumeration via different responses**
This lab is vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password. To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
Solution
First, I used Burp Suite’s proxy to intercept the request headers and content.
Then, I switched to Burp Intruder to perform a brute-force attack. I started by testing a list of usernames. I looked for an outlier response, which indicated a valid username. Once I had a valid username, I repeated the process with a list of passwords until I found the correct one.
Bypassing two-factor authentication
At times, the implementation of two-factor authentication is flawed to the point where it can be bypassed entirely.
If the user is first prompted to enter a password, and then prompted to enter a verification code on a separate page, the user is effectively in a “logged in” state before they have entered the verification code. In this case, it is worth testing to see if you can directly skip to “logged-in only” pages after completing the first authentication step. Occasionally, you will find that a website doesn’t actually check whether or not you completed the second step before loading the page.
Lab: 2FA simple bypass
This lab’s two-factor authentication can be bypassed. You have already obtained a valid username and password, but do not have access to the user’s 2FA verification code. To solve the lab, access Carlos’s account page.
- Your credentials: wiener
- Victim’s credentials carlos
Solution:
You can go to the profile page without actually using the 2FA. Just login and then go to the profile page.
Server-side request forgery (SSRF)
Server-side request forgery is a web security vulnerability that allows an attacker to cause the server-side application to make requests to an unintended location.
In a typical SSRF attack, the attacker might cause the server to make a connection to internal-only services within the organization’s infrastructure. In other cases, they may be able to force the server to connect to arbitrary external systems. This could leak sensitive data, such as authorization credentials.
SSRF attacks against the server
In an SSRF attack against the server, the attacker causes the application to make an HTTP request back to the server that is hosting the application, via its loopback network interface. This typically involves supplying a URL with a hostname like 127.0.0.1 (a reserved IP address that points to the loopback adapter) or localhost (a commonly used name for the same adapter).
For example, imagine a shopping application that lets the user view whether an item is in stock in a particular store. To provide the stock information, the application must query various back-end REST APIs. It does this by passing the URL to the relevant back-end API endpoint via a front-end HTTP request. When a user views the stock status for an item, their browser makes the following request:
POST /product/stock HTTP/1.0 Content-Type: application/x-www-form-urlencoded Content-Length: 118 stockApi=http://stock.weliketoshop.net:8080/product/stock/check%3FproductId%3D6%26storeId%3D1
This causes the server to make a request to the specified URL, retrieve the stock status, and return this to the user.
In this example, an attacker can modify the request to specify a URL local to the server:
POST /product/stock HTTP/1.0 Content-Type: application/x-www-form-urlencoded Content-Length: 118 stockApi=http://localhost/adminThe server fetches the contents of the /admin URL and returns it to the user.
An attacker can visit the /admin URL, but the administrative functionality is normally only accessible to authenticated users. This means an attacker won’t see anything of interest. However, if the request to the /admin URL comes from the local machine, the normal access controls are bypassed. The application grants full access to the administrative functionality, because the request appears to originate from a trusted location.
SSRF attacks against the server - Continued
Why do applications behave in this way, and implicitly trust requests that come from the local machine? This can arise for various reasons:
- The access control check might be implemented in a different component that sits in front of the application server. When a connection is made back to the server, the check is bypassed.
- For disaster recovery purposes, the application might allow administrative access without logging in, to any user coming from the local machine. This provides a way for an administrator to recover the system if they lose their credentials. This assumes that only a fully trusted user would come directly from the server.
- The administrative interface might listen on a different port number to the main application, and might not be reachable directly by users.
These kind of trust relationships, where requests originating from the local machine are handled differently than ordinary requests, often make SSRF into a critical vulnerability.
Lab: Basic SSRF against the local server
This lab has a stock check feature which fetches data from an internal system.
To solve the lab, change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos.
Solution:
I used Burp Suite’s Intercept feature to capture the stock checking request. Then, I sent this request to Burp Intruder.
In Intruder, I modified the stock API endpoint to http://localhost/admin. This allowed me to access the admin panel.
The response from this modified request revealed the full URL to delete the user ‘carlos’:
https://0a5700df037fdba882b5ab1e005a00d4.web-security-academy.net/admin/delete?username=carlos
SSRF attacks against other back-end systems
In some cases, the application server is able to interact with back-end systems that are not directly reachable by users. These systems often have non-routable private IP addresses. The back-end systems are normally protected by the network topology, so they often have a weaker security posture. In many cases, internal back-end systems contain sensitive functionality that can be accessed without authentication by anyone who is able to interact with the systems.
In the previous example, imagine there is an administrative interface at the back-end URL https://192.168.0.68/admin. An attacker can submit the following request to exploit the SSRF vulnerability, and access the administrative interface:
POST /product/stock HTTP/1.0 Content-Type: application/x-www-form-urlencoded Content-Length: 118 stockApi=http://192.168.0.68/adminLab: Basic SSRF against another back-end system
This lab has a stock check feature which fetches data from an internal system.
To solve the lab, use the stock check functionality to scan the internal 192.168.0.X range for an admin interface on port 8080, then use it to delete the user carlos.
Solution:
I used Burp Intruder to find the correct internal IP address for the admin panel. I set the stockApi parameter to http://192.168.0.X:8080/admin/, and then I configured Intruder to iterate the X value from 1 to 255.
Once I identified the correct X (which turned out to be 208), the full request used to delete the username ‘carlos’ was:
stockApi=http://192.168.0.208:8080/admin/delete?username=carlos
